Like ngrok or frp, but better.
TLDR
Read this forum post and this documentation.
It took me a while to find these two links, thus this blog post.
It’s free, but as with all good things these days (yes, like fly.io) they need a payment method. But then, at least Paypal works so you won’t have to reach for your credit card.
Motivation
A few weeks ago, I came across Tailscale on Hacker News. This is perfect for my use case of accessing my home computer’s RDP from anywhere, especially because my home network is behind NAT (and/or a firewall, can’t tell).
Previously this required using something like ngrok or frp. But not just that - they also needed an external server, so either your own VPS or a service provider like ngrok.com. Tailscale also promises they cannot see your data, which sounds promising.
In my personal usecase, however, there is one small issue: I use Cloudflare WARP already, and Tailscale needed a separate client (I think, for RDP). I do not know how these two clients will interact.
But it turned out that Cloudflare has this thing called Zero Trust, which I think is a corporate firewall (or security?) solution.
And it worked beautifully, on my second try.
Setup
I am deciding to skip my last attempt, during which I thought I needed cloudflared and gave up.
It turned out I was one product announcement (up in TLDR) from success.
First, get a Cloudflare account. There is a free plan.
In the dashboard, click on “Zero Trust” on the left sidebar and enroll. There is also a free plan.
Settings
I actually don’t remember my “Zero Trust” onboarding steps, but I assume the bare minimum is enough setup.
All the setting up you actually need to do:
- In Settings > Network > Firewall, turn on Proxy and then WARP to WARP.
- In Settings > WARP Client > Device enrollment, add an allow rule (I added my email).
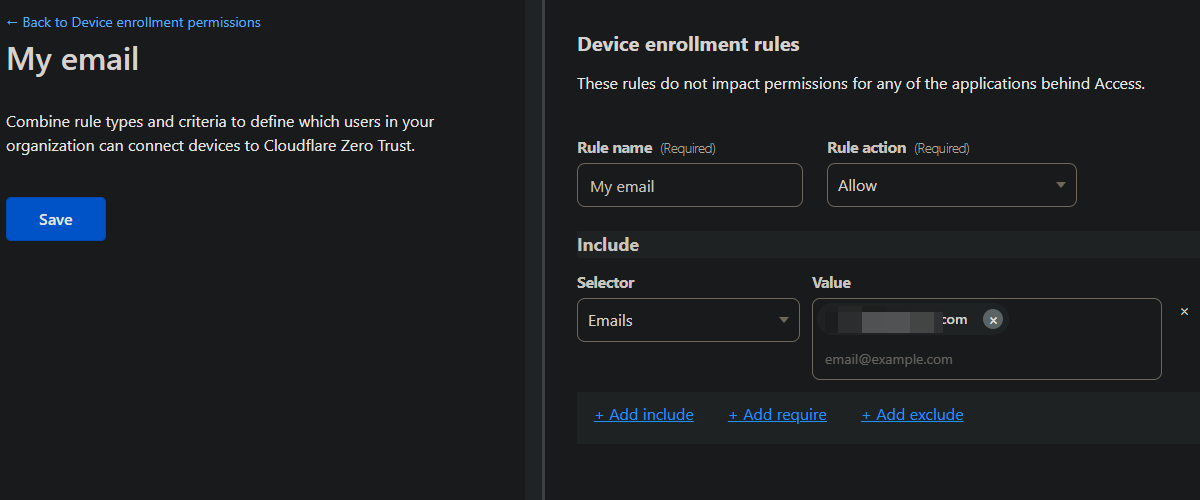
- In Settings > WARP Client > Device settings, double check the “Default” config.
- I made sure that I myself, as the user, can turn WARP off and leave my organization.
- Under Split Tunnels, make sure
100.64/10is routed through WARP.- If “Exclude IPs and domains” (the default), then click on “Manage” and remove
100.64/10from the list.
- If “Exclude IPs and domains” (the default), then click on “Manage” and remove
- Don’t forget to click on “Save profile” at the bottom!
Additionally, you may want to turn off Activity logging under Settings > Network.
Identity
Under Settings > WARP Client > Device enrollment, I think the default identity provider is OTP, a one-time password sent from noreply@notify.cloudflare.com.
However, if the email address does not already have access to WARP, there will be no email sent, even though the webpage says otherwise.
You can add an explicit rule to only allow your own email address.
Therefore, you might want to add a third-party OAuth for more timely messages or debugging. GitHub is perfect for this, because you can easily create your own third-party OAuth app - just follow Cloudflare’s on-screen instructions.
Device
Now it’s time to actually install WARP from 1.1.1.1.
Then, somewhere in Settings, log into Cloudflare Zero Trust. (On Windows it’s under Gear Icon > Preferences > Account.) You will be using the identity provider(s) above (like OTP or GitHub).
Finally, find your IPs under My Team > Devices, after you click on the device.
You’re done! Connect as usual.
PSA: Do secure your service - for RDP, Tailscale has a quick guide.
You want more
If you Google “cloudflare rdp”, Google gives you this page.
This is indeed what people might have in mind, but it does require the cloudflared CLI (which again, I do not know how it interacts with WARP).
You could also expose your web app, then clients don’t need to install WARP; they can simply connect on their browser, and Cloudflare serves as the backend identity verifier. In this case, the identity settings are in Settings > Authentication > App Launcher.
You can even have a public hostname, like docs.example.com, that points to localhost:8080, complete with Cloudflare proxying and stuff.
Check out my new blog post for how to do this: Cloudflare One.